How to Secure Microsoft Entra Conditional Access Against Legacy Authentication Attacks
Legacy authentication protocols like POP, IMAP, and SMTP are prime targets for attackers due to their weaker security posture. Despite the availability of modern, more secure authentication methods, many organizations continue to use these outdated protocols, leaving critical vulnerabilities in their Conditional Access policies. In this guide, we explore common misconfigurations related to legacy authentication in Microsoft Entra, real-world attack scenarios, and best practices for securing your environment.
Understanding Legacy Authentication in Microsoft Entra
- Legacy
authentication refers to older protocols that don't support modern
security features like MFA (e.g., POP, IMAP, SMTP) through Microsoft Entra Conditional Access policies.
Conditional Access Misconfigurations with Legacy Authentication are Common
- These protocols allow attackers to bypass security
controls, MFA bypass is one example of this.
Why
Organizations Still Use It:
- Compatibility
with older applications and devices.
- Cost
saving measures requiring users to utilize mail clients that do not
support Exchange ActiveSync if they wish to bypass using the web version
of Microsoft Outlook in favor of a desktop client.
- Service
accounts and automated processes that rely on prevent them from blocking legacy authentication.
Conditional Access Legacy Authentication Mistakes
Excluding
Groups from Microsoft Entra Conditional Access Policies
- Scenario:
Organizations often exclude Service Accounts or Admin Accounts groups from
Conditional Access policies that block legacy authentication to prevent
disruptions in workflows, utilize mail clients that are not compatible
with Exchange ActiveSync, or due to a lack of understanding of the risks
associated.
- Risk:
Attackers can target these excluded accounts through password spraying, brute force, or credential stuffing attacks.
Real-World Attack Scenario: Exploiting Legacy Authentication
- Attack
Vector: An attacker discovers that a service account is excluded from
the legacy authentication block policy. Using a credential stuffing
attack, they gain access to this account and move laterally by sending
phishing emails that pass all security checks as they come from a valid
internal account. The emails are more likely to be trusted by the end
user due to the lack of any External email flagging and coming from a
valid @companyname.com address. The attacker may also gain access to sensitive
information that allows further compromise by accessing the inbox of the
compromised account allowing further exploitation.
- Impact:
Exfiltration of sensitive data, deployment of ransomware, or persistent
access to internal systems.
Step-by-Step Guide to Securing Legacy
Authentication in Microsoft Entra
Audit
Current Conditional Access Policies
- Go
to the Microsoft Entra admin center and review existing policies.
- Identify
policies with exclusions, particularly those related to blocking legacy
authentication.
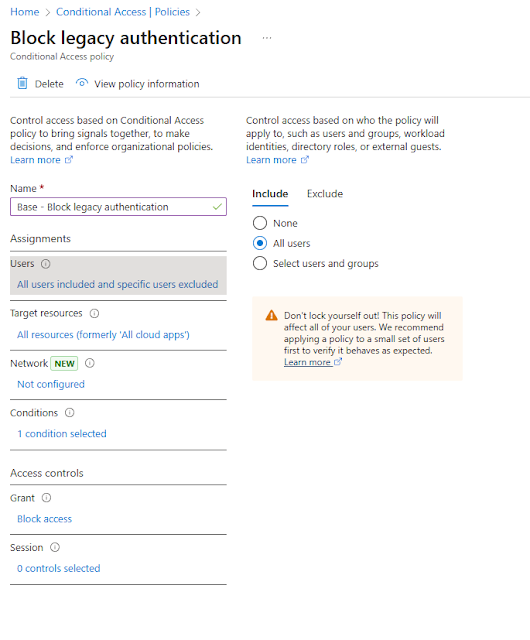
Create
a Baseline Policy to Block Legacy Authentication
- Step
1: Navigate to Conditional Access > New policy.
- Step
2: Name the policy (e.g., "Base - Block Legacy
Authentication").
- Step
3: Under Assignments, select Users and include all
users.
- Step
4: In Cloud apps or actions, select All cloud apps.
- Step
5: In Conditions, set Client apps to include only
legacy authentication protocols.
- Step
6: Under Access controls, select Block access.
- Step
7: Enable the policy.
Minimize
Exclusions with Conditional Access Exceptions
- If
exceptions are required to allow Legacy Authentication for service
accounts, make a group named “Allow – Legacy Authentication” that these
specific accounts are manually assigned to and exclude the group from the
"Base - Block Legacy Authentication" policy.
- Create
a new conditional access policy with Target Users to be the “Allow –
Legacy Authentication” group, set Target resources to “All resources
(formerly ‘All cloud apps’), and for conditions include the Legacy authentication
clients you require. Once completed create a new “named locations” and
include only the IPs that known authentication will be coming from and
apply the Network condition to this policy using that group. Be sure that
only static Ips are added to these exclusions and not entire ranges to
minimize the exposure. This will ensure that authentication without MFA
will only be allowed location known to require it, only for these legacy
protocols, and only for the specific service accounts you know will need
this capability.
Leverage
Azure AD Sign-In Logs to Detect Legacy Authentication Use
Conclusion
Additional Resources



Comments
Post a Comment