Malware Sample Analysis
- VirusTotal IOC Collection: View Collection
Extracted Phishing IOCs
Email Attachment (HTML file): View_receipt_details_U.html
EML Hash: 1ea0b4ba1728ceda14a7cab6c79b2a70a5e07e6a514e5003766e7f9a75328e3e
Malicious URLs:
- https://support-365dabwa46l17kupx.rsko-capital.com:8443/impact?
- https://sdsdsd.chiliesdigital.co.za/app/stiktk.php
Observed Domains:
- seeklogo.com
- support-365dabwa46l17kupx.rsko-capital.com
- sdsdsd.chiliesdigital.co.za
- rsko-capital.com
- chiliesdigital.co.za
- iesm.edu.pe
Behavioral Analysis and Observations
Suspicious Attachments
Taking a look at the source code of View_receipt_details_U.html we can see that it utilized seeklogo.com to pull in a Microsoft Exchange logo.
The script also contains the targets email address and appends it on the end of the request. Upon opening the html file, we quickly see why. The exchange logo from seeklogo.com is displayed while a malicious Microsoft login form is loaded in with the users email pre-filled in. How nice of them!
We also get a glimpse of the obfuscated URL without needing to do any reverse analysis from the browser inspector.
Most observed domains were routed through Cloudflare, suggesting the use of a proxy to mask the phishing infrastructure.
Domain: support-365dabwa46l17kupx.rsko-capital.com
Addresses:
2a06:98c1:58::9e (Cloudflare)
2606:4700:7::66 (Cloudflare)
2606:4700:7::9e (Cloudflare)
2a06:98c1:58::66 (Cloudflare)
162.159.140.104 (Cloudflare)
172.66.0.158 (Cloudflare)
172.66.0.102 (Cloudflare)
162.159.140.160 (Cloudflare)
Name: sdsdsd.chiliesdigital.co.za
Addresses:
2001:db8::220:1 (Reserved)
2001:db8::220:2 (Reserved)
127.220.0.11 (Private IP)
127.220.0.12 (Private IP)
Email Header Analysis
- Email Body: When initially opening the email, the body appeared mostly blank. However, when analyzing the headers we noted that the body does have contents that did not display in Outlook. It's actually quite ironic that the text includes "Your email with attachment is being deleted due to lack of information in the body of the email".
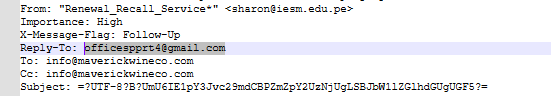
We find that while the email purports to be from [email protected] the Reply-to is [email protected].
- Mail Server: 185.192.125.150
- This IP has been reported a couple of times on abuseipdb for similar phishing scams.










Comments
Post a Comment